Sensitivity labels in Microsoft 365 are a crucial feature for organizations to protect and manage their data. These labels allow organizations to classify and safeguard sensitive information based on its level of confidentiality. By applying sensitivity labels, organizations can control access, encrypt data, apply policies, and track and monitor on sensitive information. Users can apply sensitivity labels to classify and protect their data. However, applications unfortunately cannot currently assign sensitivity labels.
As described in the Microsoft Graph API Beta documentation, for example at Update group, “Application permissions are not supported when updating assignedLabels.” This means that while individual users can apply and manage sensitivity labels, applications do not have the capability to update these labels. This restriction means that third-party applications cannot assign confidential data.
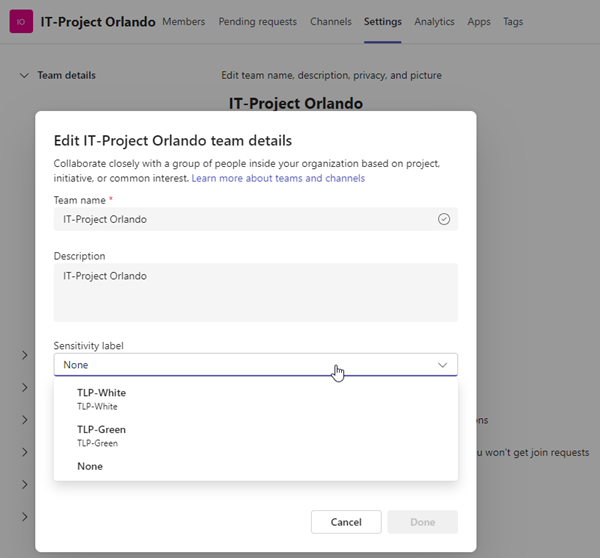
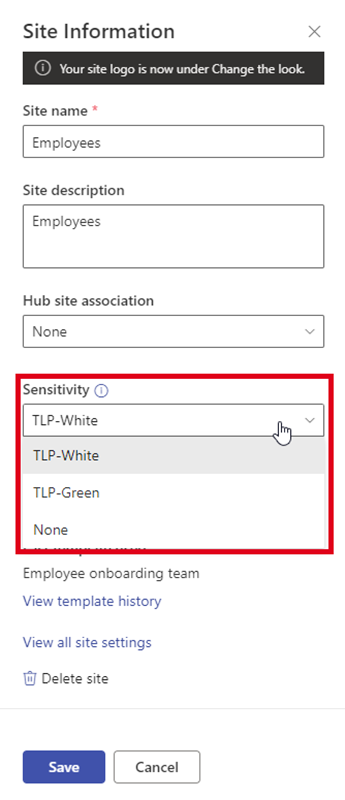
Users can assign sensitivity labels when they create a new team or SharePoint site, or assign them later.
Assign a sensitivity label in a Team
In Microsoft Teams, sensitivity labels can be assigned in the Team´s Settings.
Assign a sensitivity label in a SharePoint site
For a SharePoint site, site admins can set sensitivity labels in the Site information, as here.
Microsoft Graph with app permissions
For organizations who are developing a custom or third-party app, there are currently methods to use sensitivity labels in the Microsoft Graph Beta, for example List sensitivityLabels, and more. Sensitivity labels can be read and partially managed, but unfortunately cannot be assigned to a team or SharePoint site. The documentation at Update group says clearly:
“Application permissions are not supported when updating assignedLabels.”
We have built a small PowerShell script using an application authorization in the $header to test this functionality to verify this.
# Testing assign a sensitivity label to a team
# $header contains a Graph app token with permissions for Group.ReadWrite.All and InformationProtectionPolicy.Read.All
$labelid = "<some-label-id>"
$groupid = "<some-group-id>"
$body = @{
assignedLabels = @(
@{
labelId = $labelid
}
)
} | ConvertTo-Json
$url = "https://graph.microsoft.com/beta/groups/$groupid"
result = Invoke-RestMethod `
-Method Patch `
-Uri $url `
-Body $body `
-ContentType 'application/json' `
-Headers $header `
-ErrorAction Stop
$result.value | ft
With app permissions, we get an “InternalServerError”, saying “Unauthorized”, and “App-only token is not supported” (as expected)
{
"error": { "code": "InternalServerError",
"message": "{…Unauthorized:…App-only token is not supported…}",
"innerError": { … }
}
}The only workaround for doing this programmatically currently is to set the labels with a user authenticated flow, script, or app, with delegated permissions and not with app permissions.
We do not understand why Microsoft does not allow applications to set sensitivity labels. Even if there are security concerns, this functionality would be incredibly helpful for ISVs to enhance security support. We hope Microsoft will add these app permissions sooner or later.